Using IIS to generate SSL and private key for use on Linux Systems
Windows 2008 Server , Windows 7 Add commentsThis week I needed to renew the SSL certificate for our OpenVPN server. the process according to the docs required using OpenSSL to generate a private key, which will then be used to generate a CSR, which will then be used to register your SSL, and you then need to get the certificate (CRT) file, a CA bunble (crt) file, and a private key (pem) file to install on the OpenVPN server.
Now I am used to dealing with Windows and IIS, and dealing with SSL is a breeze on windows, but as is usually the case when it comes to Linux, simple tasks like this suddenly become 10 x more work and as my Linux skills are almost zero that made the task even more arduous.
I had a go at doing everything with OpenSSL but ended up generating invalid SSL certs that did not work, so I then thought to myself, why not just use IIS to generate the CSR and get the SSL cert and then just export it from there into a format I can use on Linux, this seemed like it would be a much quicker solution and it was, here are the steps.
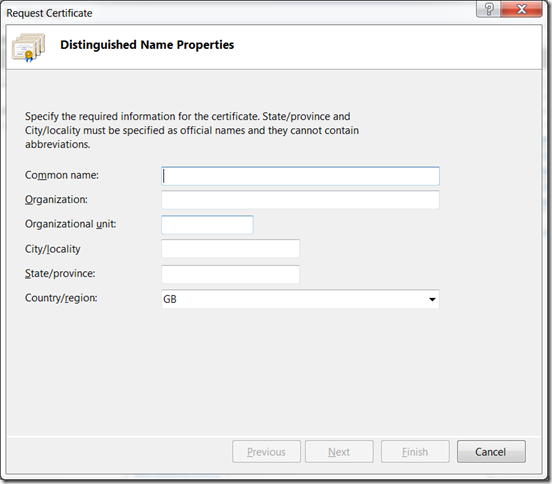
Using IIS7 on any machine, generate your CSR in the usual way, I did this on my local Windows 7 machine.
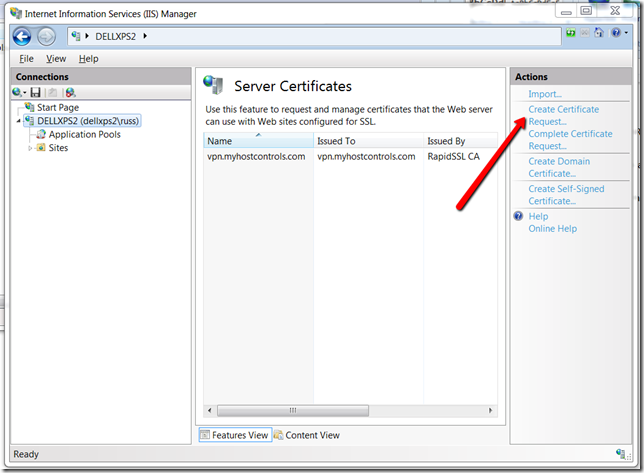
Now take your CSR and register your SSL certificate in the usual way, when you get it back, install it on IIS from above section using "complete certificate request"
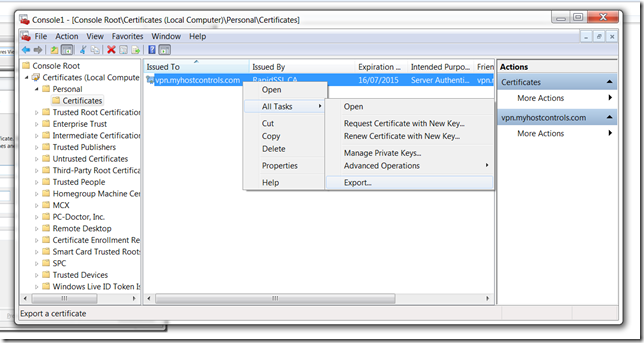
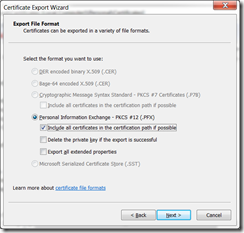
Once you have your SSL installed in IIS, you now need to export the SSL and the private key as a pfx file.
Open MMC.exe and add the certificates snap-in, now browse to the personal>certificates and export your SSL cert
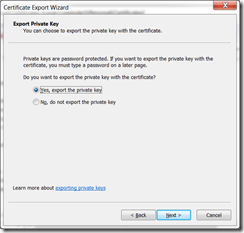
choose to export the private key and include all certificates
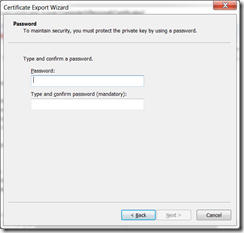
Your private key password is your windows password that you are current logged in with.
For Windows systems this PFX file will be everything you need, however on Linux systems (such as open VPN) you will need separate private key files.
This is where you need to use OpenSSL.
Using command line.
Export the private key file from the pfx file
openssl pkcs12 -in filename.pfx -nocerts -out key.pem
Export the certificate file from the pfx file
openssl pkcs12 -in filename.pfx -clcerts -nokeys -out cert.pem
Remove the passphrase from the private key
openssl rsa -in key.pem -out server.key
Using XCA GUI
XCA is a handy GUI for open SSL, you can download it here http://sourceforge.net/projects/xca/
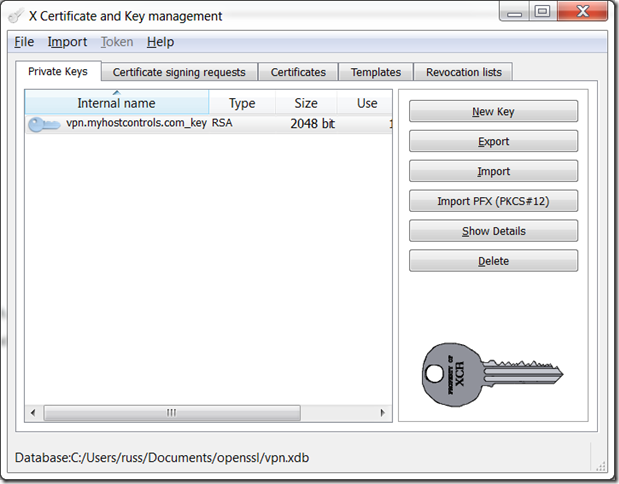
On the Private Keys tab choose "Import PFX", this will import everything from your PFX file.
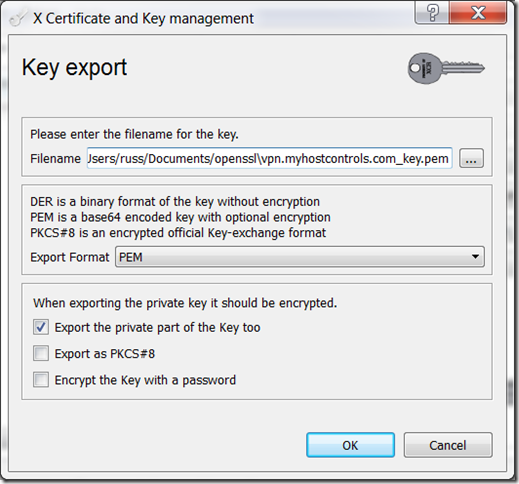
Now select your newly imported private key, and click export to get your PEM file.
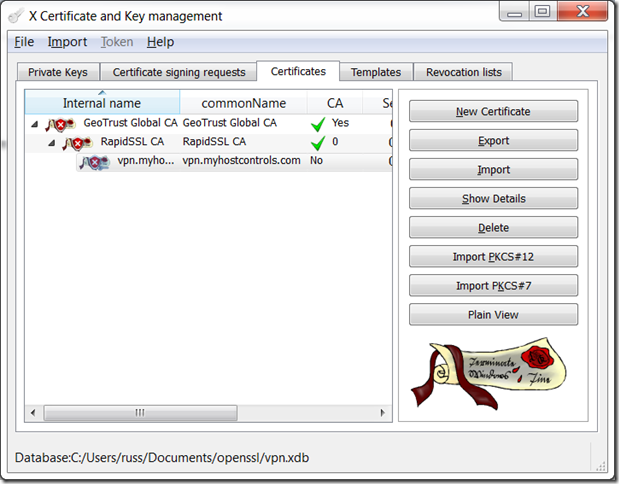
Now select your certificate and export that in required format, although in most cases the certificate file you received from the CA will be sufficient.
If you need a CA bundle, then export all the certs from the root, or use the intermediate cert you would have received from the CA.










Feb 21, 2015 at 7:08 PM Excellent!I'm glad with this confirmation. I just happen to have had the same thought and was searching around for possible show stoppers. Thanks for the step by step instructions!