Cybercriminals have set their sights on iOS users, using malware to steal face scans and gain access to Apple device users' bank accounts. This is believed to be the first of its kind in the world. A group of cybercriminals who speak Chinese, known as GoldFactory, have been distributing smartphone apps infected with trojans since June 2023. The latest version, GoldPickaxe, has been around since October. GoldPickaxe and GoldPickaxe.iOS target Android and iOS devices respectively. They trick...
Security
Beware of disposable phone numbers
So, what are disposable phone numbers? These are virtual phone numbers that are not permanently assigned to a specific individual or device. Anyone can purchase a temporary number from a service provider online. It is not tied to a physical SIM card or phone line contract. Users of these phone numbers can receive SMS or calls via the provider’s app or website. We’ll go into the various reasons below why people would need to use disposable phone numbers and why you should beware of disposable...
Protect Domains that do not send email
If you own a domain name that you do not use for sending emails, it is essential that you configure these domains correctly so that email servers around the world know not to accept emails from these domains. Even if you are not using a domain to send email, without taking these steps, there is nothing to stop spammers any cybercriminals from sending spoofed email impersonating your domain, pretending to be from you and thus damaging your reputation. This is very common for businesses to use...
Voice Cloning – The latest cybersecurity threat
Voice Cloning - A Growing Cybersecurity Threat Just when you think you’re reasonably on top of all the cyber threats out there, new ones emerge. Say hello to voice cloning. Or don’t say hello to it because you don’t want a scammer to have your voice. Voice cloning made headlines recently when scammers called a frantic mom saying they had kidnapped her daughter and demanded $1 million in ransom. They “put her on the phone” and the mother was certain it was her daughter on the other...
Urgent scam warning for anybody using Gmail , Outlook or Hotmail
An expert security company has issued a warning to users of Microsoft Outlook, hotmail and Google Gmail after reporting a massive 240% rise in email phishing scams. Cyber defence firm BlueVoyant has spoken about "dynamic phishing" and "smishing" scams due to their reputation for being difficult to identify. BlueVoyant has listed typical warning signs in order to help people spot dodgy emails. One technique that scammers often use is multiple redirect paths after a user has clicked on an email...
LastPass Hacked – How serious is it & Things You May Not Know
If you use LastPass as your password manager, I recommend reading this post in full.If you know anyone who uses LastPass, forward this to them.Even if you do know about the LastPass hack, I still recommend you read this, as there will be information here that you may not know about and risks you have not thought of In case you are not aware LastPass got hacked Back In August 2022 and then AGAIN in November and all customer password vaults have been stolen. This is also not the first time they...
Beware: Paypal Money Request Scam is back
If you have a paypal account, then literally anyone with an email address can request money from you. That's the double-edged sword with PayPal - it's simple to set up and use for legitimate purposes, but fraudsters can take advantage of that ease of use to perpetrate scams on the unsuspecting public. The PayPal Money Request scam has been around for a long time, but occasionally the scammers will often revert to using old tricks, so consider this a friendly reminder, this one has made a...
Hackers using “push bombing” to bypass your MFA/2FA
Multifactor authentication (MFA) is the gold standard in offices around the world and 2FA is the standard for end users. We all know the drill: you use your username (often your email address) and, perhaps, as the password, the name of your first dog and your kids DOB. Not very foolproof, and not recommended, but often the end user isn’t too worried. In their mind, they know that if the hacker does figure out their crappy password using various tools or techniques, they still must find their...
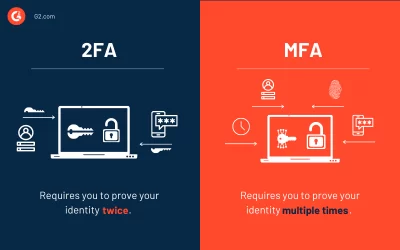
What is the difference between 2FA and MFA ?
Cybersecurity is a complex topic and if you are the average layperson, you likely have found yourself asking "What is the difference between 2FA and MFA ". In simple terms, Two-Factor Authentication (2FA) requires users to demonstrate exactly two distinct methods of authentication, whereas Multi-Factor Authentication (MFA) requires users to demonstrate a MINIMUM of two distinct methods of authentication but can be more. So, all 2FA is MFA, but not all MFA is 2FA. If you are new to the world of...
New Android malware bypasses multi-factor authentication to steal your passwords
Cybersecurity researchers uncover MaliBot, a powerful new Android malware that steals passwords, bank details and cryptocurrency wallets from users. Besides being able to siphon passwords and cookies of the victim's Google account, the malware is designed to swipe your 2-factor authentication codes from the Google Authenticator app as well as exfiltrate sensitive information such as total balances and seed phrases from Binance and Trust Wallet apps. The malware has been detailed...











Recent Comments