Cybersecurity is a complex topic and if you are the average layperson, you likely have found yourself asking “What is the difference between 2FA and MFA “.
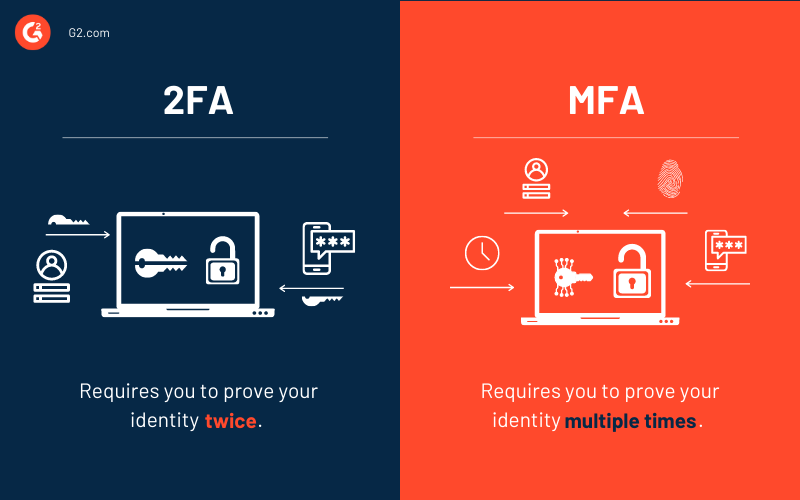
In simple terms, Two-Factor Authentication (2FA) requires users to demonstrate exactly two distinct methods of authentication, whereas Multi-Factor Authentication (MFA) requires users to demonstrate a MINIMUM of two distinct methods of authentication but can be more. So, all 2FA is MFA, but not all MFA is 2FA.
If you are new to the world of cybersecurity, terms such as MFA and 2FA may appear rather cryptic to you. Sometimes MFA and 2FA are used interchangeably, but although similar, they are not the same thing. Both acronyms have been in wide use for years and happen to be an inseparable part of online security, so let’s once and for all clear up the confusion around MFA and 2FA.
Preliminary Definitions
In order to fully comprehend what MFA and 2FA are, you have to understand two concepts: that of authentication and that of a factor of authentication.
Authentication is a process during which a security system decides if the person who tries to log in is exactly who they claim to be.
The preceding definition entails that a security system has to find a way to ensure that the person who tries to log in as Bob is indeed Bob and not someone pretending to be Bob. The security system should not grant access to some oher person using Bob’s credentials. So how can a security system know that the person is Bob?
Well, Bob has to successfully present adequate evidence of his identity and then and only then will he be granted access.
A factor of authentication is a piece of evidence that a user has to present to prove they are who they claim to be.
The three basic Factors of Authentication are:
- Knowledge Factor – represents what you know, e.g. a password
- Possession Factor – represents what you have, e.g. a phone, a security token
- Inherence Factor – represents who you are, e.g. your fingerprint or eye retinal pattern
MFA vs. 2FA
Multi-Factor Authentication (MFA) is a type of authentication that requires two or more factors of authentication.
Two-Factor Authentication (2FA) is a type of authentication that requires exactly two factors of authentication.
Two-Factor Authentication is, therefore, a subset of Multi-Factor Authentication, and the following two sentences are true:
- Every Two-Factor Authentication is Multi-Factor Authentication
- Not every Multi-Factor Authentication is Two-Factor Authentication

Why Is One Factor Not Enough?
The Knowledge Factor is the most commonly used factor of authentication. A password you enter every time you log in to an application is an example of the Knowledge Factor. Unfortunately, passwords have long proved insufficient in the contemporary world. Simply put, passwords are not secure enough.
Cybercriminals invented a wide range of methods to intercept and hack somebody’s password, from phishing to keylogging, to rainbow table attacks. If passwords are your sole line of defense against unauthorized access, then you better enable Multi-Factor Authentication in your workforce before it’s too late along with a password manager.
How Introducing More Factors Improves Security?
MFA adds more factors of authentication and therefore eliminates security threats associated with low security of passwords. You can think of every factor as an additional lock, with varying levels of difficulty of breaking them. If you introduce Two-Factor Authentication (2FA) to your users’ login experience, then even if a malicious third party manages to break the weak lock (password), they will not be able to open the door because the strong lock (e.g. the Mobile Push authentication request method) will stop them.
The Mobile Push authentication method is an example of the Possession Factor. Mobile Push is one of the methods your users can use if they install a mobile authentication app. Assuming the attacker already broke your password, now they have to steal or gain remote access to your phone, which isn’t impossible but much harder than cracking a password. Stealing or gaining access to your phone requires additional steps on the attacker’s side, which in turn means more time for you to react. Simply tapping DENY on your phone will stop any malicious attempt at breaking into your account.
PC Mag
Human Error And More Factors of Authentication
Nobody’s perfect. It’s human to err. Sometimes you work under stress or pressure and it’s so easy to get distracted. Attackers know this and they will try to attack you when you are the weakest. You can make a mistake that will cost you your data and money. Two-Factor Authentication significantly mitigates the probability of human error but does not eliminate it. Introducing yet another factor of authentication will make your authentication even stronger and the chances of human error are negligible.
One way to further reinforce your MFA is turning on fingerprinting in your Authenticator.
With fingerprinting turned on, your Mobile Push Multi-Factor Authentication may look as follows:

Again, adding more factors of authentication is like adding more locks to your door, each lock harder to crack than the other. In the login example above, three factors of authentication were used: Knowledge Factor (password), Possession Factor (phone), and Inherence Factor (fingerprint). Since three factors were used, the preceding is an example of Multi-Factor Authentication but not Two-Factor Authentication.
Enable MFA/2FA Now
To reiterate, MFA involves introducing more factors of authentication to the process of authentication. 2FA is a subset of MFA that involves using exactly two factors of authentication. Using just one factor in the form of a password is not secure enough, and that’s why you have to enable Multi-Factor Authentication in your company.
Time is of the essence. Now that you understand what MFA/2FA is and know how insecure using only passwords in your company is, enable MFA before it’s too late! Improving security should be your number one concern now.
Russ Michaels







