We have all heard by now of the term phishing and how it works, where a generic email is sent with an encrypted URL or attachment and when it’s clicked “BOOM”… you have been caught. But, over the last few years we have seen a significant rise in spear phishing.
Spear phishing is technically the same but with a more direct and targeted approach. The hackers will spend time looking into an individual or a small group of people’s own lives, interests and job role and create an email which seems legitimate and interesting, interesting enough to click. The aim is to either infect devices with malware or convince victims to hand over information or money. In this article we will learn what is spear phishing and how to avoid it
The Federal Bureau of Investigation conducted detailed research in to spear phishing and reported that most spear phishing is directed at businesses who use “wire transfers as a common method of transferring funds for business purposes”. This is also known as the BEC Scam which is defined as a “…sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
Where phishing attacks began as Nigerian prince scams in the mid-1990s, today they have morphed into well-researched and targeted campaigns that are both highly effective and incredibly difficult to stop.
Phishing versus spear phishing
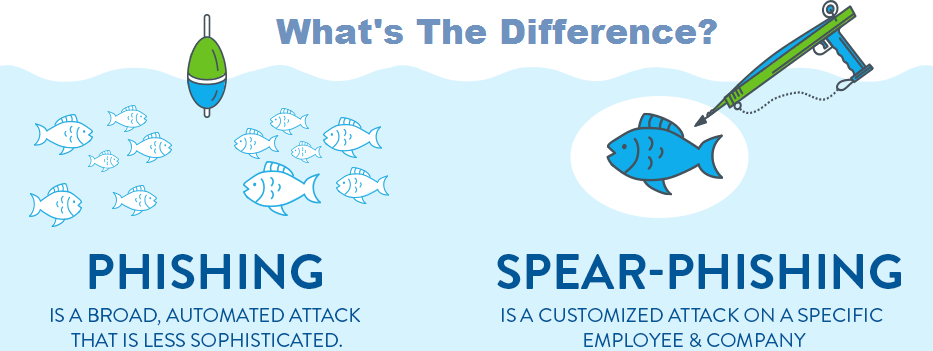
While regular phishing campaigns go after large numbers of relatively low-yield targets, spear phishing aims at specific targets using specially emails crafted to their intended victim. “Phishing is just kind of generic, low-tech, not targeted attacks,” says Aaron Higbee, cofounder and CTO of anti-phishing firm Cofense (previously known as PhishMe). “They don’t particularly care about who their target is. They’re just casting a wide net trying to snare as many people and as many companies as possible.”
“Spear phishing is a campaign that was purposefully built by a threat actor with a goal of penetrating one organization, and where they will really research names and roles within a company,” Higbee adds.
Where mass phishing primarily involves using automated off-the-shelf kits to gather credentials en masse using faux log-in pages for common banking or email services or spread ransomware or cryptomining malware, spear phishing attacks are more complicated. Some targeted campaigns involve documents containing malware or links to credential stealing sites to steal sensitive information or valuable intellectual property, or to simply compromise payment systems. Others avoid malicious payloads and instead use social engineering to hijack processes for a small number of large payouts via a single or series of bank transfers.
The “from” part an email is often be spoofed to make it look like it’s from a known entity or from a domain that looks similar to yours or your trusted partners. For example, the letter “o” might be replaced with the number “0,” or the letter “w” might be changed to “ш” from the Russian alphabet.
While older spear phishing campaigns used to simply contain the malicious documents attached in the email as is or perhaps in a zip file, criminals have adapted their methods. Higbee explains that many malicious documents are now housed on legitimate sites such as Box, Dropbox, OneDrive or Google Drive as threat actors know these are unlikely to be blocked by IT. “We’re also starting to see phishing attacks that are trying to compromise API tokens or session tokens in order to get access to an email box or to get access to a OneDrive or SharePoint site.”
Reconnaissance the key to spear phishing
Along with extremely focused targeting, spear-phishing campaigns contain a large reconnaissance element. Threat actors might start with emails harvested from a data breach, but supplement that with a host of information easily found online. The Nigerian criminal group known as London Blue, , has even used legitimate commercial lead generation sites to gather information on CFOs and other finance department employees.
Social media such as LinkedIn and Twitter provide insight into roles, responsibilities and professional relationships within an organization, and thus help inform who is best to both target and impersonate. Company websites might provide insight into processes, suppliers and technology, while the likes of Facebook and Instagram might provide personal insight into potential targets that could be leveraged.
“Fraudsters make use of background information in order to create a credible narrative,” says Oz Alashe, CEO of cybersecurity training and awareness platform CybSafe. “Combining the data gained from an organization’s team page, a LinkedIn profile, a Twitter profile, and a Facebook profile, a criminal can usually capture quite a detailed picture of their victim. They might use your name, information about where you work, who you bank with, a recent payment you’ve made, information about your family and friends, and any other private information they can find.”
Spear phishing and whaling
Spear-phishing attacks targeting high-level executives are often known as whale phishing attacks, and usually involve an attacker attempting to impersonate the CEO or similarly important person within the company with the aim of using superiority to coerce the victim into making payments or sharing information. Studies suggest executives are more likely than other employees to fall victim to such attacks. A recent Rapid7 experiment managed to fool three-quarters of the CEO’s it targeted.
“Executives at the top of an organization are more likely to be targeted than other staff, be under pressure and juggling time-critical tasks and often suffer from what psychologists call attentional bias, and may underestimate the spear-phishing threat,” explains Alashe. “They embody a dangerous combination of being both highly valuable and highly available to criminals. For cybercriminals, the potential rewards from targeting an executive compared to junior members of an organization make it worth the time invested in researching and crafting these highly-targeted emails.”
Targeted attacks that look to abuse processes such as payroll or invoicing are commonly known as business email compromise (BEC). Security firm Agari has recently found examples of scammers targeting HR departments to convince them to change existing payroll direct deposit accounts to those set up by the criminals. A more common example is attackers pretending to be suppliers and requesting a change in invoicing details.
Targeted attacks involving texting or voice calls are known as smishing and vishing, respectively, and follow similar patterns as email-based attacks.
Spear phishing tools
While perpetrators are criminal organizations or nation-states – Ukraine recently thwarted a suspected Russian attack against the State Judicial Administration – the tools are largely the same. Attacks relying solely on social engineering and business transaction could even be done through a basic email account from a regular provider without any extra tooling.
“Anyone can do this, ultimately,” says Tony Gee, associate partner at Pen Test Partners. “Looking like the right name of the CEO is often enough to convince people and can be performed by someone with a Gmail account. The more sophisticated attacks, you need to have infrastructure to support the attack, but most phishing kits and backends are broadly the same. Instead of blanket sending out lots of emails, you’re just sending out one or two and you’re crafting them in a better way.”
Higbee of Cofense says that many off-the-shelf phishing kits are becoming increasingly good at automated personalization features. Many dark web criminal services now have people who will do research and scrape social media at scale on behalf of criminals – meaning attacks might not be as targeted as they first appear.
“It feels like it’s a spear phish because it’s very intimate, but we’re seeing many companies getting several versions of this on a monthly basis,” says Higbee. “It feels like you are being targeted specifically when in reality it is just the a more advanced automated phishing kit.”
He admits that the other side, however, is criminals might use more generic phishing tools and methods as the first wave of an attack so as not to reveal and burn more advanced techniques because more simple methods often work well enough.
Why is spear phishing effective?
According to the latest edition of Symantec’s Internet Security Threat Report, spear phishing was the primary infection vector among organized crime actors and employed by 71 percent of groups in 2017. Wombat’s State of the Phish study found 53 percent of infosec professionals reported experiencing spear phishing in 2017, with the majority of those facing one to five targeted attacks per quarter.
“If you think about opportunities to interface with a company, or to get something to run on the inside of the company, email is still the gateway,” says Higbee. “Because that is the door inside of an organization, it seems like phishing is going to be a bit the vector for quite some time.”
Recent and notable attacks include volunteers and employees of Hillary Clinton’s presidential campaign being targeted as part of the Democratic National Committee attack and European manufacturer Leoni AG losing $45 million after its finance department was duped intro transferring funds into the wrong account.
The effectiveness of spear phishing comes down to a combination of both technical and psychological reasons. “Spear phishing emails are quite hard to detect because they are so targeted,” says Gee. “They look like normal business emails with normal business chitchat, so it’s really hard for spam detection systems to realize it’s not a genuine email. Spear phishers exploit that because you don’t want your spam protection blocking genuine emails as end users get frustrated and business processes start to fall down.”
Gee adds that criminals might spend time building up the reputation of IP addresses and email domains by sending legitimate traffic and emails for a time to ensure they avoid blocking lists.
The effectiveness of spear phishing also comes down to the human element and the fact they contain a heavy element of social engineering that plays on how people think and act. “Trust is a natural and beneficial part of the human psyche – an innate and necessary part of forming relationships,” says Alashe. “It’s this ingrained capacity for trust which phishers like to abuse. People are significantly more likely to comply with requests from authority and trusted figures.”
“Written with enough personalisation, with the right tone, and with the right message, spear phishing is incredibly difficult to spot,” Alashe continues. “A high degree of personalization dramatically increases the trustworthiness of emails. The more personal information is present in an email, the more likely a victim is to believe that the email is authentic.”
How spear phishing works
While spear phishing emails are highly targeted and therefore likely different from organization to organization, unifying trends should raise red flags among users. The most obvious warning sign is an incorrect email address or one that looks similar to one you expect but is slightly different. However, email addresses can be spoofed or may not be noticeably different without close inspection.
“One of the most common spear-phishing traits involves exploiting a sense of urgency,” says Liviu Arsene, senior e-threat analyst at Bitdefender. “Whether it’s about clicking a URL to change an expired password without which you can no longer access an account or opening an attachment (usually an invoice, shipping tracking document, or updated policy agreement), the end goal is to instill a sense of urgency in doing a task while using a familiar language.”
The urgency will often be coupled with an urge to break company policy or norms, fast-tracking payments without the usual checks and procedures. They may also use emotive language to either invoke sympathy or fear; the impersonated CEO might say you’re letting them down if you do not make the urgent payment, for example.
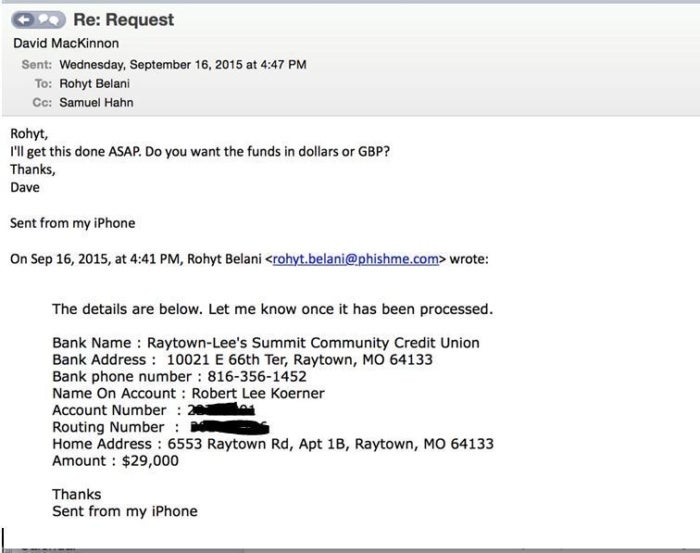
Another trait to look out for is the wording and terminology. Does the email include business lingo or expressions not normally heard within your company or from your staff? “A lot of companies we speak to, when they experience CEO fraud, actually detect it because of really silly little things,” says Gee. “Like in the UK we used terms like ‘bank transfer’ whereas a lot of [fraudsters] will use the term ‘wire transfer,’ or if the boss signs off emails ‘thanks’ whereas they would typically sign off with ‘cheers.’”
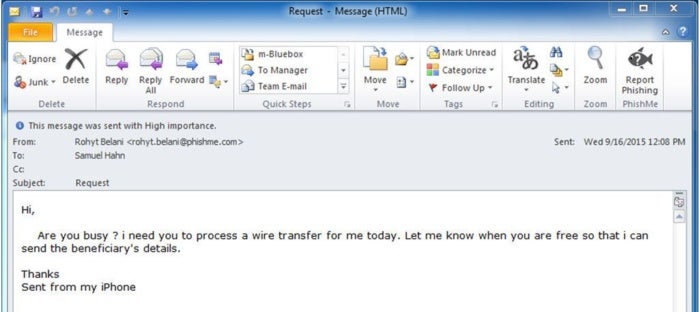
He adds that often emails will contain files – or links to files – that require macros to be enabled. “That’s a warning sign. Most macros are benign, but would you normally expect to receive that? If you do, do you need to enable macros to do this task?”
Spear-phishing prevention
Organizations can put both technical and human controls into place to mitigate the threat of spear phishing. Along with standard controls such as spam filters, malware detection and antivirus, companies should consider phishing simulation tests, user education, and having an established process for users to report suspicious emails to the IT security team.
“One of the simple ways that businesses can counter things like business email compromise is just by simply tagging emails when they come in at the gateway and put ‘external’ in the subject line,” explains Pen Test Partner’s Gee. “That’s not necessarily going to stop an attack, but it is potentially going to allow end users to think something might not be right.”
1- Be mindful – With all your details online now, your information can be sourced and used very easily. Don’t give away too much, and never post any personal details like address, phone number or bank details. Still enjoy it, post them funny photos, tell your friends you had the best day at the beach with your family, even tell everybody that you had a burrito for your lunch … but be careful. If you get an email about a “free burrito” from your favourite takeaway by the sea side, it’s probably not coincidence! Be aware and stay vigilant.
2- Check the links – Spear phishing emails usually have links in them, asking you to click to change a password, verify details or sign up to something new and exclusive. But before you click, the best thing to do is to check the URL by hovering over the link. If it’s a phishing scam, you can bet the URL will be something completely irrelevant to the email and sometimes followed by a line of random numbers and digits.
3- Use Logic – Why would your work colleague want to know your bank details? Why would your boss send you a link to click a link to view your phone bill? They most likely wouldn’t, so if in doubt at all, contact that person directly and verify if they sent the email. And if you do get a phishing email, delete it immediately! Better safe than sorry.
Check out these 11 phishing prevention tips for best technology practices, employee education and social media smarts
Source: , CSO, Metacompliance







